-
Platform
-
-
Collective Defense Platform
Leverage NDR powered by behavioral analytics and crowdsourced attack intelligence to secure your enterprise network
-
IronRadar Threat Intel Feed
Proactively block adversary infrastructure targeting your organization
-
Overwatch Services
Extend your SOC with our dedicated team offering 24/7/365 NDR services.
-
Collective Defense Platform
-
-
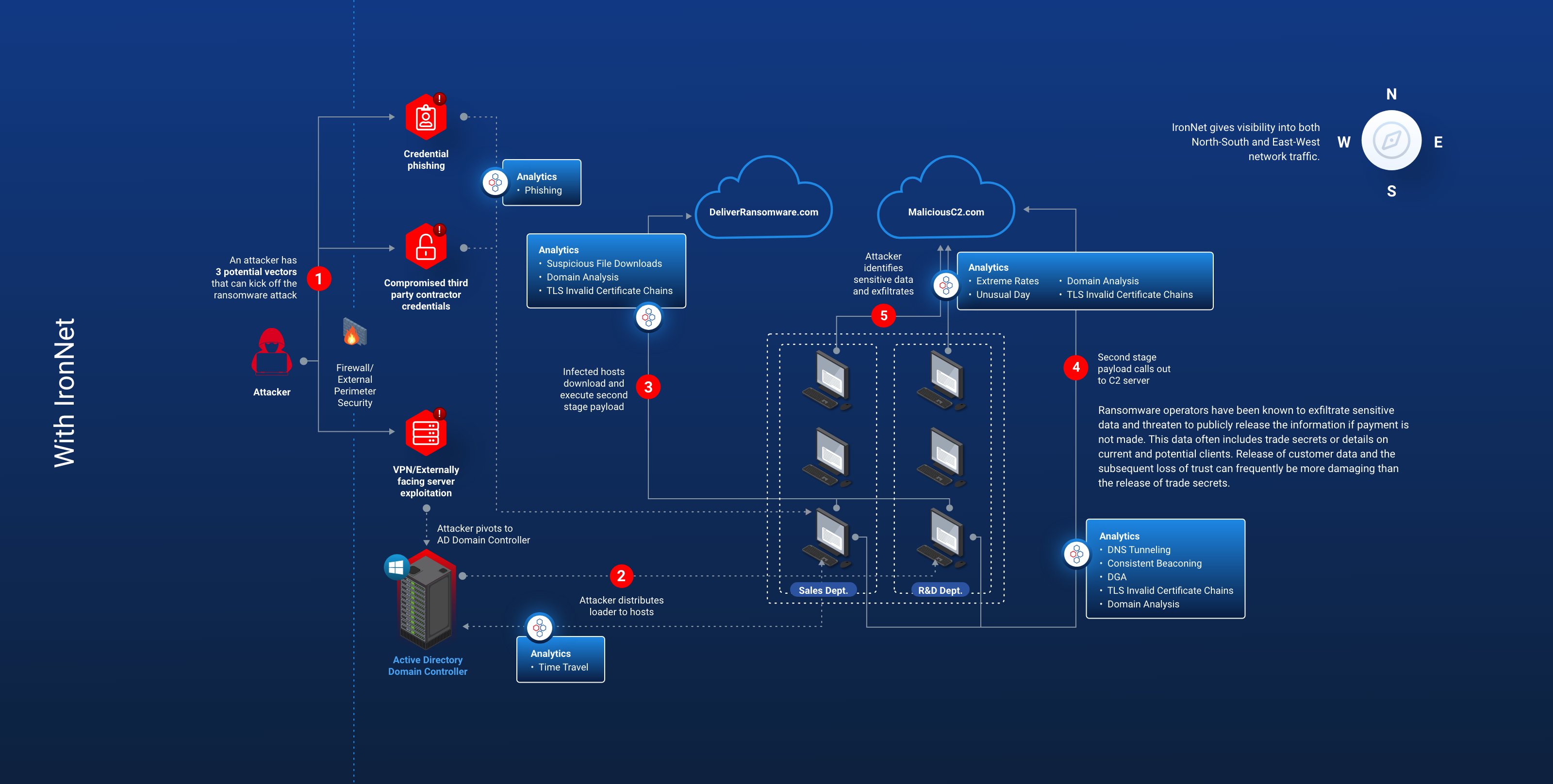
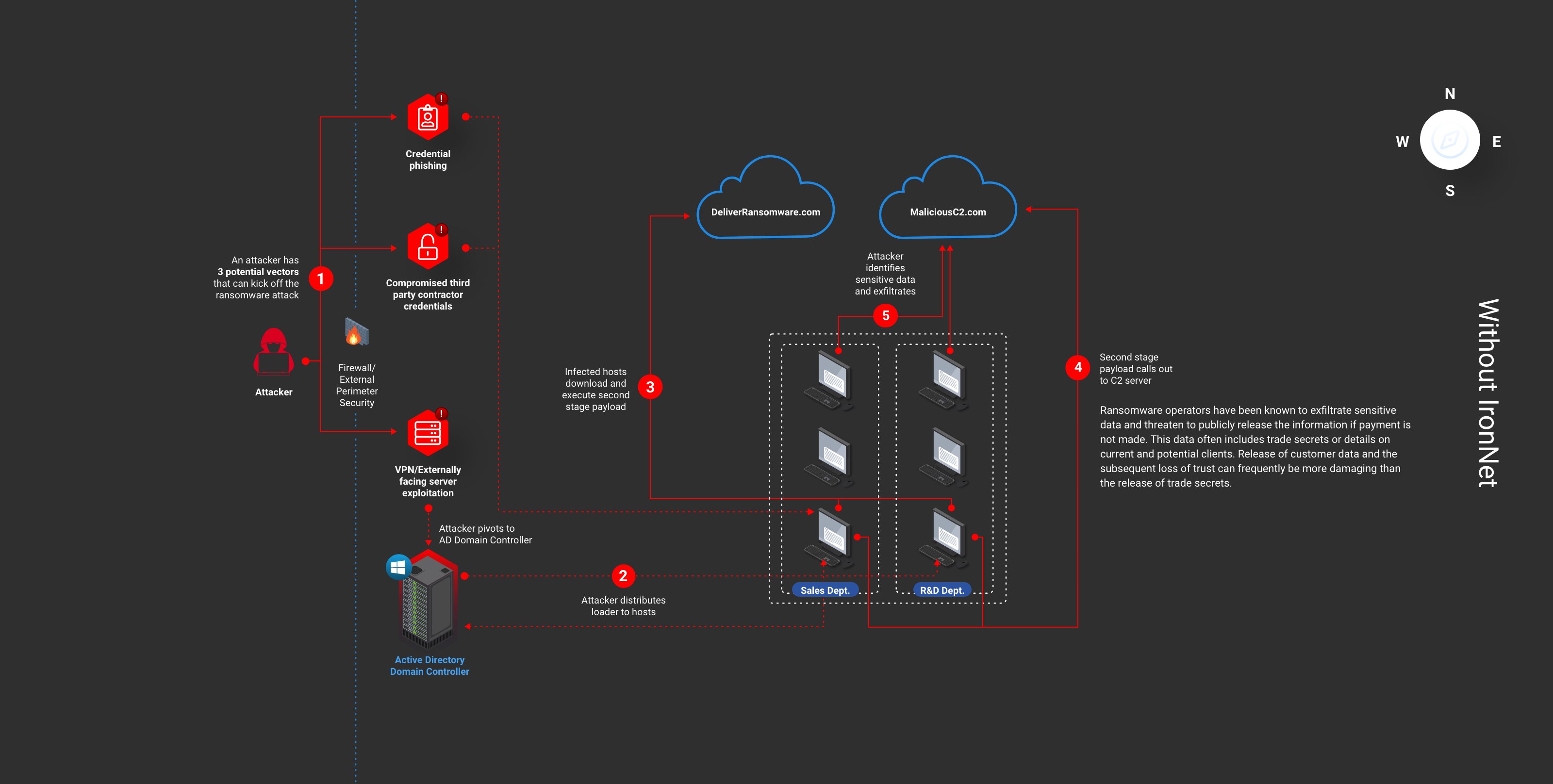
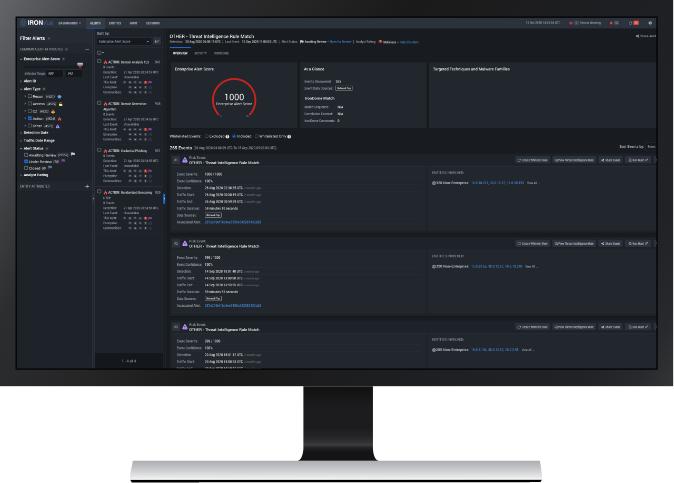
Delivering Collective Defense through NDR
![Collective Defense DataSheet Preview (1)]() Data SheetRead more
Data SheetRead more
-
Delivering Collective Defense through NDR
-
-
Why IronNet
-
-
Use Cases
See how organizations benefit from IronNet
-
For SOC Analysts
Reduce alert fatigue and build a more proactive defense
-
For CISOs
Maximize current investments and strengthen your security posture
-
Use Cases
-
- Industries
-
Company
-
-
IronNet Successfully Completes Financial Restructuring
Press ReleaseStronger, Private, and Ready to Defend.Read more
-
IronNet Successfully Completes Financial Restructuring
-
Resources
-
-
IronRadar Reforged
BLOG POSTExplore IronRadar’s new service offerings designed to empower cybersecurity teams with proactive threat intelligence.Read more
-
IronRadar Reforged
- Request Demo
-
Platform
-
-
Collective Defense Platform
Leverage NDR powered by behavioral analytics and crowdsourced attack intelligence to secure your enterprise network
-
IronRadar Threat Intel Feed
Proactively block adversary infrastructure targeting your organization
-
Overwatch Services
Extend your SOC with our dedicated team offering 24/7/365 NDR services.
-
Collective Defense Platform
-
-
Delivering Collective Defense through NDR
![Collective Defense DataSheet Preview (1)]() Data SheetRead more
Data SheetRead more
-
Delivering Collective Defense through NDR
-
-
Why IronNet
-
-
Use Cases
See how organizations benefit from IronNet
-
For SOC Analysts
Reduce alert fatigue and build a more proactive defense
-
For CISOs
Maximize current investments and strengthen your security posture
-
Use Cases
-
- Industries
-
Company
-
-
IronNet Successfully Completes Financial Restructuring
Press ReleaseStronger, Private, and Ready to Defend.Read more
-
IronNet Successfully Completes Financial Restructuring
-
Resources
-
-
IronRadar Reforged
BLOG POSTExplore IronRadar’s new service offerings designed to empower cybersecurity teams with proactive threat intelligence.Read more
-
IronRadar Reforged
- Request Demo
.png)