
I absolutely am a believer in the power of threat intelligence. The challenge with threat intelligence, however, is that the information often isn’t very tailored for a particular organization. Some threat intel feeds or platforms are timely. Others are relevant. Still others are actionable. The trick for today’s threat intelligence providers is to capture information that’s all three things at once – that is, timely, relevant, and actionable. Only by doing so can we turn reactive threat intel into proactive threat intel.
What do I mean by “proactive threat intelligence”? To me, it means information that includes situational context of the incipient stages of an attack campaign, thereby giving analysts time to prioritize alerts and act quickly. It means that an analyst doesn’t stop at the question: “What should I be looking for based on this information?” Instead, they also can ask, “What are the organizations to my left seeing? What about those to my right?” Armed with this breadth of intel – and with real-time situational awareness – an analyst gains a clearer picture of how attackers are taking advantage of vulnerabilities across a sector or supply chain.
Indeed, we can't defend everywhere, at the same time, all the time, so we have to focus our attention on the alerts that truly matter.
Cyber threat detection “left of boom”
So let me illustrate how we go from reactive to proactive threat intelligence. Consider the old tried-and-true cyber kill chain created by Lockheed Martin. It has stood the test of time, now complemented from a technical perspective by the MITRE ATT&CK® framework.
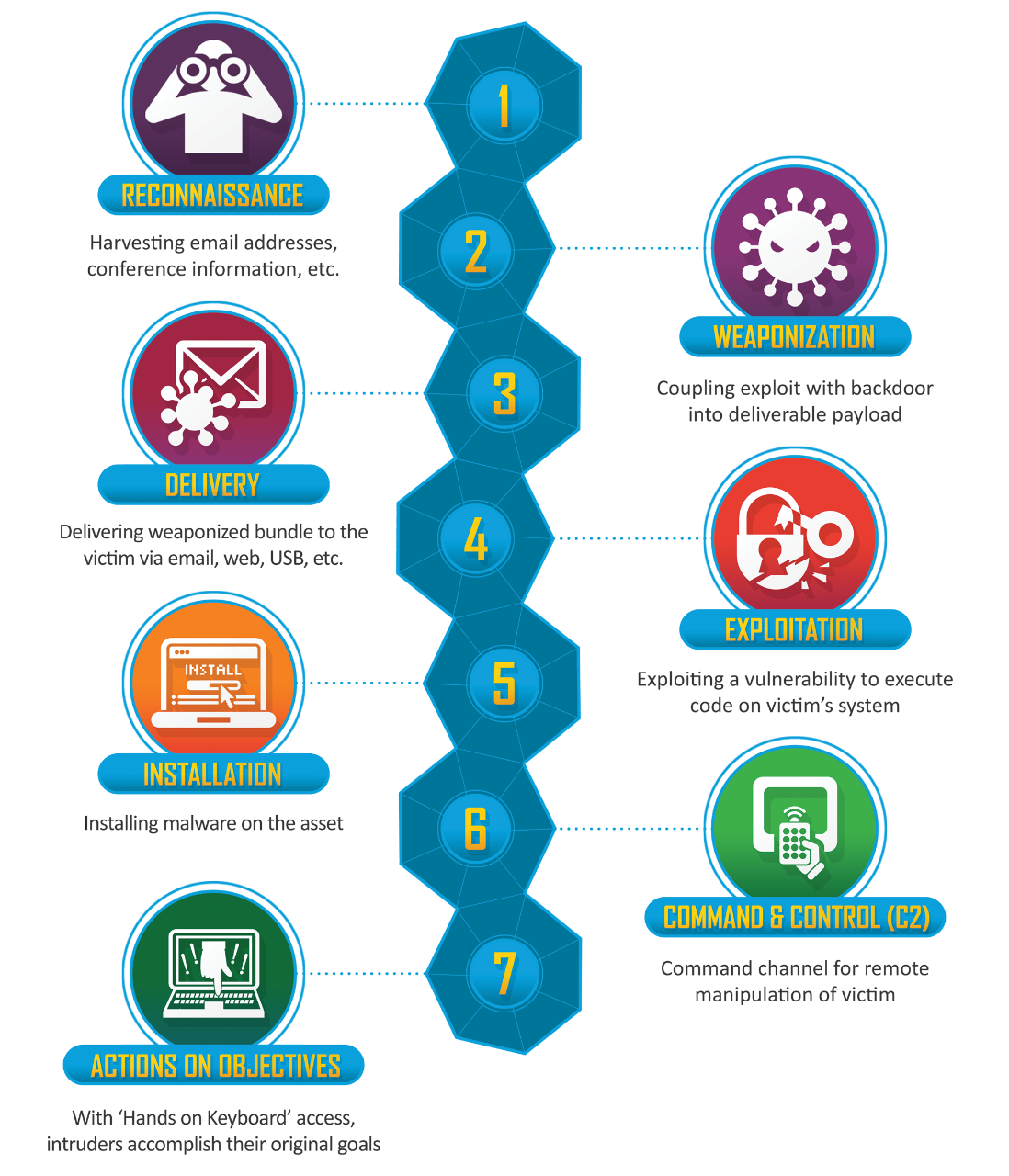
While absolutely essential for a defense-in-depth cybersecurity strategy, most threat intel we get today covers activity that happens “right of boom.” In other words, after an organization already has been compromised. The threat intel extracts the indicators of compromise (IOCs) that led to the incident and shares that information with the community. From there an organization can conduct a kind of cyber pulse check to see if it, too, has been compromised.
How do we get to “left of boom”? There are a few ways to reach this ideal stage of threat detection, and I've personally been involved in many of them. For now, I’d like to focus on the weaponization stage. How do we identify the adversaries? How do we detect their infrastructure before it's used against us? The answer is behaviors. Only by detecting adversarial behaviors on the network – what we call indicators of behavior – can cyber defenders shift the advantage in their favor by stopping adversaries before they reach their endgame: exfil, disruption, or system control.
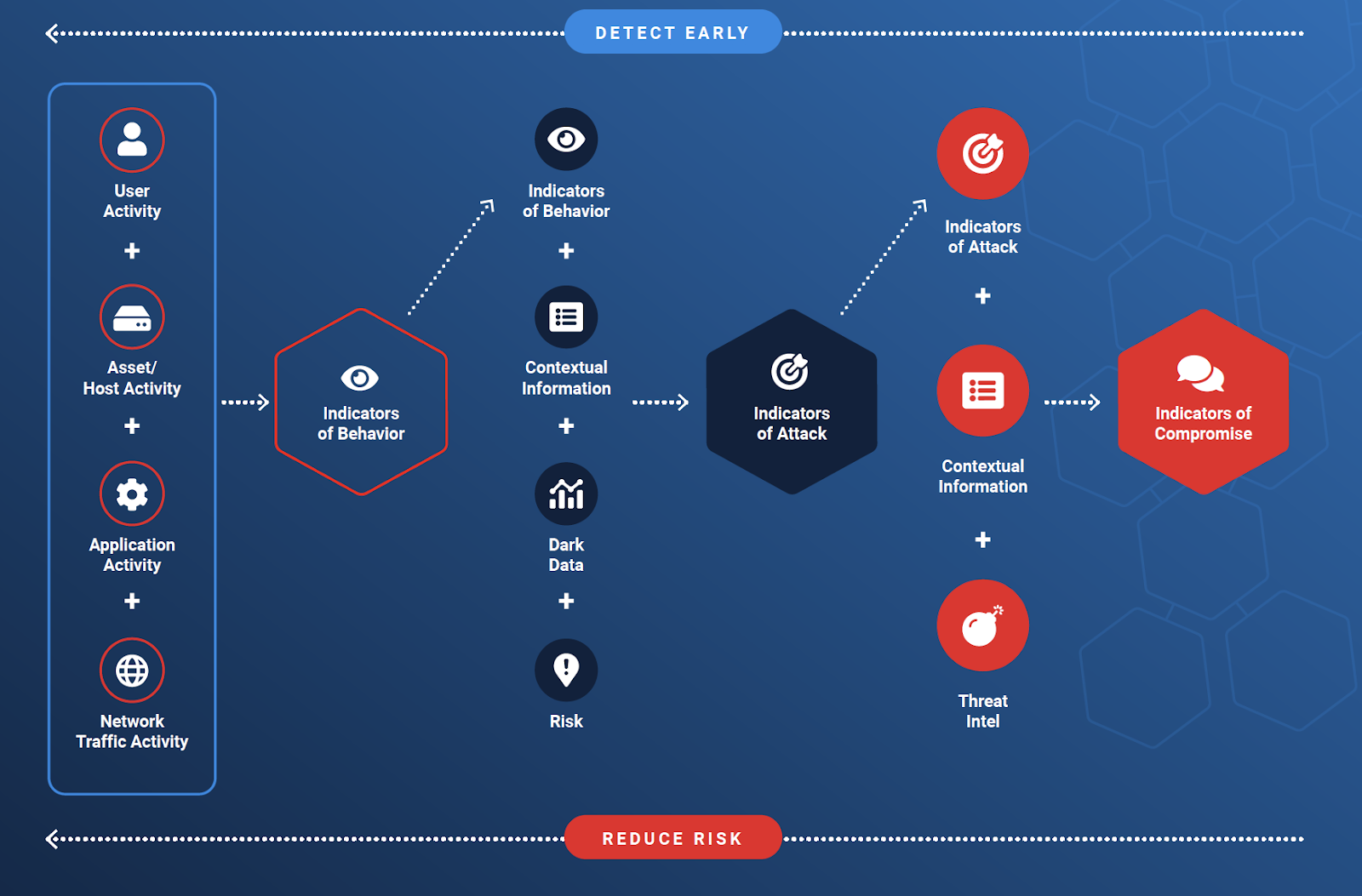
IronRadar: the power of seeing malicious infrastructure as it’s being set up
The IronNet cyber operations center (CyOC) – with some of the best threat hunters in the world – asked these same questions. One day, one of our elite hunters responded to a phishing alert but discovered there was no phishing attack. When he drilled into the alert, he discovered the phishing infrastructure as it was being stood up yet not quite ready for prime time.
Could you imagine the value here? That is, being able to detect “left of boom” as the adversary was setting up a C2 server and making sure the malicious plumbing, so to speak, was working before turning on the nozzle. From there, we knew what the cyber criminals were going to be targeting based on the tools that they were stockpiling in that particular server, and we were able to proactively block that threat. Just as important, we were able to protect a whole bunch of other companies by sharing this proactive threat intelligence so the attack on their networks never happened.
That’s what I mean by “left of boom,” proactive threat intelligence. Since then, IronNet has created the IronRadar C2 threat intel feed to give organizations an efficient and easy way for security teams to proactively block threats and improve detection by automatically ingesting data on the latest known – as well as new and unreported – attacker infrastructure. It provides security operations, incident response, and cyber threat intelligence teams with everything they need to quickly detect C2 servers before they are used in an attack and take action against today’s most sophisticated attackers.
Why detecting “left of boom” matters for the Oil & Gas industry
This proactive threat intelligence is even more important for critical infrastructure industries, like oil and gas, especially in light of the current geo-political context. The operational technology (OT) networks and industrial control systems (ICS) that are embedded in critical infrastructure have historically been closed-off, hard-wired, and safeguarded by proprietary communication protocols.However, the convergence of IT and OT has changed everything so that cyber adversaries can attack the IT environment with the goal of exploiting OT. In fact, Dragos reported in its 2021 ICS Cybersecurity Year in Review that, “external connections to OT spiked upwards, more than doubling to 70%” potentially “due to the high demand for remote access in the wake of the COVID-19 pandemic.”
The IT/OT convergence has made detecting common IT attack vectors critical for preventing an adversary from moving laterally and using the stolen credentials to access the OT domain. Behavioral analytics are key to detecting these early threats on the IT network, and, in fact, many OT attacks can be stopped and blocked by preventing initial access to the enterprise network.
.png)

