Microsoft releases a report on its disruption of a Russian cyber-espionage group called SEABORGIUM (COLDRIVER) that has targeted over 30 organizations since the beginning of 2022, primarily in NATO countries and in the sectors of defense consulting, NGOs, IGOs, think tanks and higher education.

At IronNet, we look to behavioral analytics to detect unknown threats on enterprise networks before adversaries succeed at their endgame: exploitation or exfiltration. First, we do the threat detection groundwork needed to spot abnormal network activity across our customers’ networks. Second, our IronDefense NDR expert system scores these alerts, prioritizing the most interesting events to help cut down on alert fatigue. Finally, we take a Collective Defense approach to crowdsourced threat intelligence exchange in real time.
The September IronNet Threat Intelligence Brief
This ability to analyze and correlate seemingly unrelated instances is critical for identifying sophisticated attackers who leverage varying infrastructures to hide their activity from existing cyber defenses. As reported in the September Threat Intelligence Brief, our analysts review alerts from millions of data flows that are ingested and processed with big data analytics. We apply ratings to the alerts (benign/suspicious/malicious) and immediately share them with IronDome Collective Defense participants.
Here is a snapshot of what we discovered across the IronDome communities in August, showing 2,878 correlated alerts across IronDome participant environments:
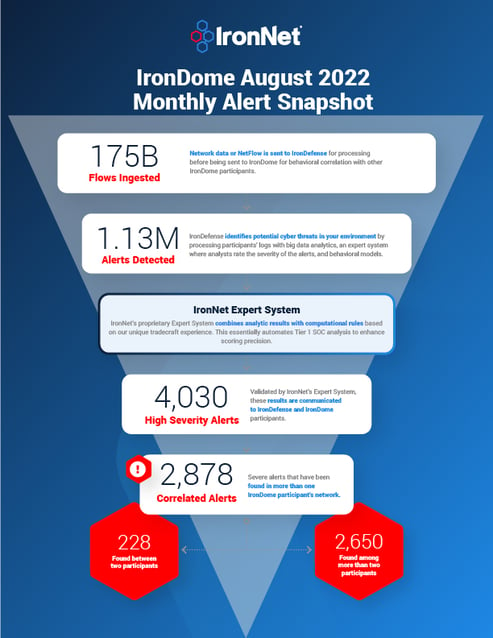
Given the unique cross-sector visibility and Collective Defense capabilities of IronDome, we are able to highlight the most frequent behaviors each month, in turn enabling us to track trends over time. For August, the most frequent behavior analytics were DNS Tunneling (1,688), New and Suspicious Domains (433), and Credential Phishing (185).
Analysis of IOCs
In addition to correlated alerts, significant IronDome community findings revealed 1,393 Indicators of Compromise (IOC) that may pose risk to IronDome participant environments. For example, we analyzed the malicious domain www.mp3juice[.]zone, a domain that was recently created on 07/07/2022 and hosts mp3 copyrighted content available for download and has been flagged as malicious. OSINT associates this domain with malware that is associated with the Command and Control, C2, Sauron Malware, It is recommended that traffic analysis be conducted and the domain be blocked.
All the IOCs we analyzed are used to trigger alerts that are mapped to the Cyber Kill Chain to identify the stage and progression of the threat. They can be used to create detection rules for network, endpoint, or other security tools currently deployed to mitigate cyber risk in each IronDome participant’s environment.
See the September Threat Intelligence Brief for the full list of recent IOCs.
The bigger picture of Collective Defense
Every month, IronNet’s expert threat analysts create threat intelligence rules (TIR) based on significant community findings from IronDome, malware analysis, threat research, or other methods to ensure timely detection of malicious behavior targeting an enterprise or other IronDome community participants.
In August, we created 53,671 threat intel rules of our 433,411 created to date. Some examples of this month’s research related to indicators associated with Cobalt Strike beacon payload distribution and C2, IOCs related to Robin Banks phishing kits, and IOCs related to Raccoon malware.
This combination of behavior-driven and IOC signature-based detection, alert ranking, and sharing ensures IronDome participants have the broadest view of threats facing their enterprise.
APT29 MagicWeb post-compromise capability
Researchers state APT29 remains highly active and has been executing multiple highly-targeted campaigns concurrently against government orgs, NGOs, IGOs, and think tanks in the US, Europe, and Central Asia. They also state they uncovered a post-compromise capability called MagicWeb used by APT29 to maintain persistent access to compromised environments.
You can see the latest industry news in the full brief or check out IronNet’s threat intelligence hub.


.png)



