As we look back on October, we have much to report on: from Russia upping their nation-state attacks by groups such as APT29 (aka, Nobelium) and APT28 (aka, FancyBear) to Microsoft’s report detailing APT29’s latest phishing campaign targeting the IT supply chain. Abusing the trust in IT supply chain relationships, APT29 can piggyback on access resellers have to their customers’ systems.

At IronNet, we look to behavioral analytics to detect such unknown threats on enterprise networks before adversaries succeed at their end-game: exploitation or exfiltration. When it comes to ransomware attacks and other types of attack campaigns, early detection is critical. First, we do the threat detection groundwork needed to spot abnormal network activity across our customers’ networks. Second, our expert system scores these alerts, prioritizing the most interesting events to help cut down on alert fatigue. Finally, we take a Collective Defense approach to crowdsourced threat sharing in real time.
The November IronNet Threat Intelligence Brief
This ability to analyze and correlate seemingly unrelated instances is critical for identifying sophisticated attackers who leverage varying infrastructures to hide their activity from existing cyber defenses. As reported in the November Threat Intelligence Brief, our analysts review alerts from millions of data flows that are ingested and processed with big data analytics. We apply ratings to the alerts (benign/suspicious/malicious) and immediately share them with IronDome Collective Defense participants.
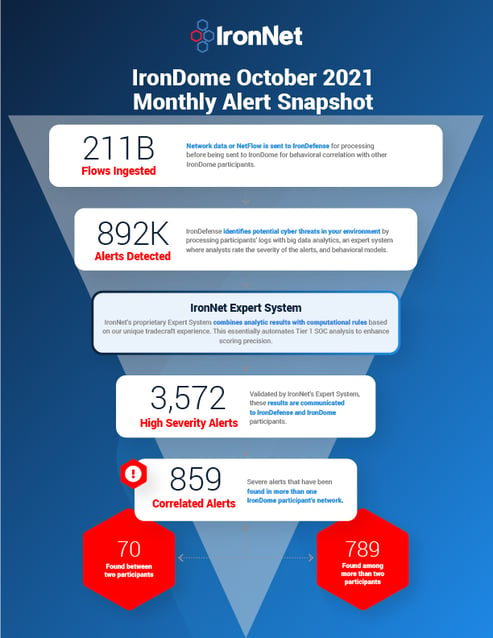
Here is a snapshot of what we discovered across the IronDome communities in October, showing 429 correlated alerts across IronDome participant environments:
Given the unique cross-sector visibility and collective defense capabilities of IronDome, we are able to highlight the most frequent behaviors each month enabling us to track trends over time. For October, the most frequent behavior analytics were External Scanning (652), Suspicious File Downloads (418), and Beaconing (77).
Analysis of IOCs
In addition to correlated alerts, significant IronDome community findings revealed 530 Indicators of Compromise (IoC) that may pose risk to IronDome participant environments. For example, we analyzed the malicious freefiles-8[.]de, a suspicious file identified as a malicious DownloadGuide by numerous security vendors and is most commonly software bundlers or installers for applications.
All the IoCs we analyzed are used to trigger alerts that are mapped to the Cyber Kill Chain to identify the stage and progression of the threat. They can be used to create detection rules for network, endpoint, or other security tools currently deployed to mitigate cyber risk in each IronDome participant’s environment.
See the November Threat Intelligence Brief for the full list of recent IoCs.
The bigger picture of Collective Defense
Every month, IronNet’s expert threat analysts create threat intelligence rules (TIRs) based on significant community findings from IronDome, malware analysis, threat research, or other methods to ensure timely detection of malicious behavior targeting an enterprise or other IronDome community participants.
In October, we created 6,048 threat intel rules of our 275,115 created to date. Some examples of this month’s research related to indicators associated with malware delivery domains for Gafgyt, AgentTesla, Sabsik, Dridex, and Nekark malware, as well as IoCs surrounding Chinese state-sponsored APT41 threat group.
This combination of behavior-driven and IoC signature-based detection, alert ranking, and sharing ensures IronDome participants have the broadest view of threats facing their enterprise.
APT29 targets MSPS vulnerabilities discovered
As I mentioned, Microsoft reported that Russian state-sponsored threat group APT29 (aka, Nobelium) has targeted over 140 managed service providers (MSP) in the U.S. and Europe since May 2021. APT29 successfully breached 14 MSPs. Technology service providers are APT29’s main target in hopes to access privileged accounts of upstream providers in order to move laterally in cloud environments using access resellers have to their customer’s systems. To accomplish this, APT29 chained together artifacts from 4 different providers to reach their target.
You can see the latest industry news in the full brief or check out IronNet’s threat intelligence web page.

.png)


