If you know one thing about IronNet you know this: we believe in Collective Defense. And while the benefits of this approach are well documented, misconceptions remain.
One common misconception relates to data sharing in a collective defense ecosystem. Specifically, there is concern that a data sharing platform may compromise data privacy compliance. The reality, however, is that operational controls provide reliable protection on these fronts — and sharing threat data is the only way to increase our defenses to a level to which we are truly effective against coordinated, well-funded nation-state attacks.
The data shared in IronNet’s Collective Defense platform, IronDome, goes through a rigorous minimization process to ensure anonymity before it reaches the IronDome — all the while preserving data ownership in the hands of the participating company or organization. What's more, the anonymized data is encrypted upon transit to and from the ecosystem. In other words, no company must give up data ownership or privacy to reap the benefits of working together: improved visibility across the threat landscape, faster time to response, and improved effectiveness of existing cybersecurity investments.
Threats on networks can be detected without needing any corporate or personally identifiable information (PII). This level of security holds true to companies with on-premise, cloud, or hybrid networking environments. Instead, only data associated with anonymized threat events and metadata are needed to create a real-time picture of the threat landscape. By its definition, metadata is a set of data that describes other data; it does not provide the actual message content from a communication.
As Ted Schlein, Partner at Kleiner Perkins, says in the on-demand webinar Why cybersecurity isn’t a post-pandemic luxury:
You can protect and share data at the same time. You don’t need the specifics; you need the meta information because you’re looking for patterns. Realizing that your safety and security are only as good as your other brethren in other industries is key. You have to defend in real-time.
Specifically, we take the following steps to ensure data minimization:
1. Data protection
IronNet uses a rigorous, automated process to prevent disclosure of sensitive information. We leverage customer input and security expertise to identify metadata that contains sensitive information, in turn eliminating enterprise-identifying information such as IP addresses, domains, intellectual property (IP), and personally identifiable information (PII).
2. Encryption
All data sent to IronDome, our Collective Defense solution, is encrypted before transmission. This encrypted information is pushed to the IronDome data repository where it is stored and analyzed. Data within the IronDome system is encrypted while at rest. All transmissions back to a participant’s IronDefense system(s) are encrypted in the same manner.
3. Data enrichment protection
Within CloudConnect, the purpose of enrichment is to retrieve up-to-date information about external domains and IP addresses to enhance the behavior detections of IronDefense. These enrichments require constant updating and connection to the public internet. The enrichments are then used to prioritize the IronDefense detections.
4. Collective Defense correlation
Within IronDome, Collective Defense correlations identify how metadata from one instance of IronDefense is related to metadata from another instance of IronDefense. This includes correlating IP addresses, domains, and behavioral metadata from IronDefense’s detections. These correlations drastically improve the efficiency of the alert triage process.
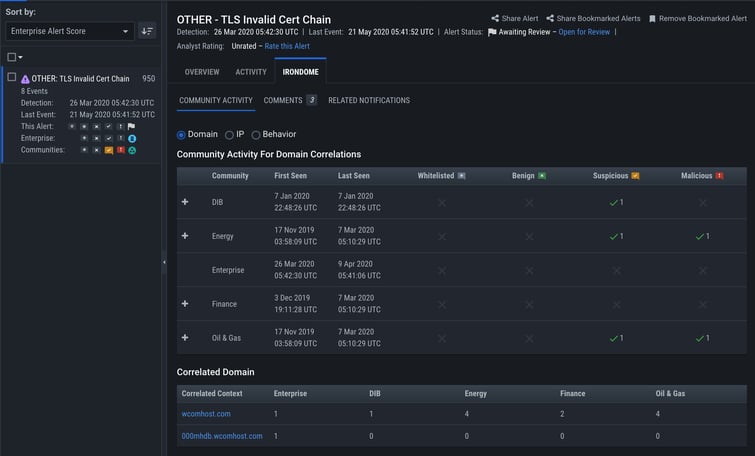
IronNet’s user interface displays community correlations and analyst assessments.
Additional data protection measures
In addition to these efforts, we prevent the disclosure of sensitive information by restricting data access according to privacy best practices and regulatory requirements.
In practice, this means we restrict access to raw IronDome messages to IronDome data scientists, threat researchers, and analytics teams for the purposes of developing and applying IronDome analytical capabilities and improving the effectiveness of security protections. IronNet has achieved SOC 2 Type II certification, ensuring strong security policies and an internal controls environment for this type of work.
On the client side, no access to raw IronDome messages is provided. Instead, participants receive derived threat insights from IronDome that inform threat correlation, analyst assessment and commentary, and risk scoring analysis to locally detected behavioral patterns by the participant’s IronDefense instance. In other words, you get the insight without the risk.
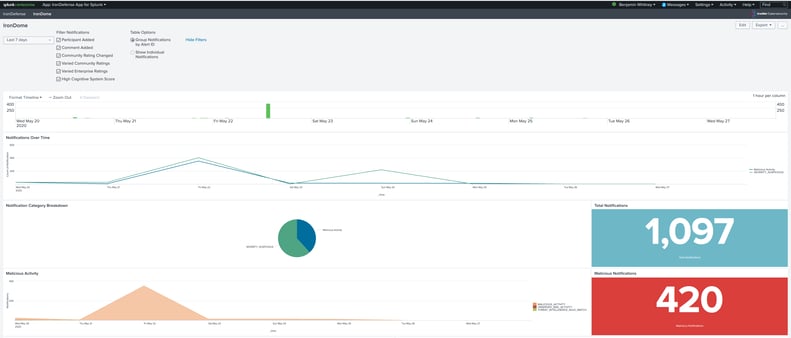
IronNet’s IronDefense App for Splunk displays IronDome
community notifications to prioritize analyst workflow.
Cybersecurity in the data sharing economy
Collective Defense is gaining traction based on the simple concept that we’re stronger together. But our approach to data protection is anything but simple. IronNet has developed strict data protocols to ensure the utmost security of sensitive information while delivering the full benefits of a Collective Defense ecosystem.
.png)
